soc 2 physical security|What is SOC 2 : Tagatay SOC 2 physical security requirements encompass the policies, procedures, and controls designed to protect an organization’s physical assets and sensitive information. These . Azumi Mizushima. Actress: GAR-189. Menu. Movies. Release Calendar Top 250 Movies Most Popular Movies Browse Movies by Genre Top Box Office Showtimes & Tickets Movie News India Movie Spotlight. TV Shows. What's on TV & Streaming Top 250 TV Shows Most Popular TV Shows Browse TV Shows by Genre TV News.
PH0 · What is SOC 2? Complete Guide to SOC 2 Reports and Compliance
PH1 · What is SOC 2? Complete Guide to SOC 2 Reports
PH2 · What is SOC 2? A Beginners Guide to Compliance
PH3 · What is SOC 2
PH4 · What Is SOC 2 Compliance?
PH5 · Simplify SOC 2 compliance with the right physical
PH6 · SOC 2 Physical Security Requirements: Meaninga and Usage
PH7 · SOC 2 Compliance Definition & Checklist
PH8 · SOC 2 Academy: Physical Security Controls
PH9 · SOC 2
PH10 · Guide: The physical security requirements of SOC 2
The Microsoft Teams Add-In populates a link automatically as soon as you add a user to an event causing people to join the Microsoft Teams meeting versus a third-party (such as webex or zoom). I have discovered a way to disable this on an individual basis (via webmail and disabling it from Outlook settings) but I need an organization .
soc 2 physical security*******Best practices for achieving SOC 2 physical security compliance. Achieving SOC 2 compliance in the realm of physical security requires a meticulous approach, an . SOC 2 is an auditing procedure that ensures your service providers securely manage your data to protect the interests of your organization and the privacy of its clients. For security-conscious .SOC 2 physical security requirements encompass the policies, procedures, and controls designed to protect an organization’s physical assets and sensitive information. These . SOC compliance is the most popular form of a cybersecurity audit, used by a growing number of organizations to prove they take cybersecurity seriously. A SOC 2 report will provide you with a . Social engineering is a serious threat to many organizations, but it’s often a thought that gets put on the back burner. If you’re .
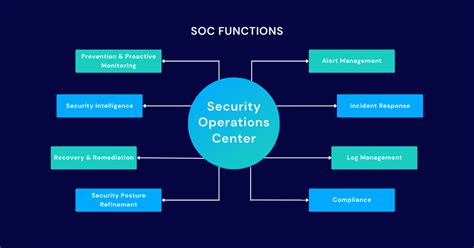
SOC 2 compliance improves data security best practices : By adhering to SOC 2 compliance guidelines, organizations can improve their security posture and better .
SOC 2 is a security framework that specifies how organizations should protect customer data from unauthorized access, security incidents, and other vulnerabilities.The basic SOC 2 compliance checklist covers the following security standards: Access controls: Prevent unauthorized access with logical and physical restrictions on assets. . SOC 2 Type II accreditation provides peace of mind that proper procedures are in place to ensure data stored within the Genetec system is secure, private and confidential. It also provides independent . When it comes to data security, the SOC 2 Trust Services Criteria (TSC) is one of the most critical standards. These standards cover everything from physical .What is SOC 2? SOC 2 (Service Organization Control Type 2) is a cybersecurity compliance framework developed by the American Institute of Certified Public Accountants (AICPA) that helps manage customer data within the cloud. SOC 2 is an auditing procedure that specifies high standards of data security on five “trust service principles”—security, availability, .
This type of SOC often has a physical location within the organization’s premises and is staffed by in-house security experts responsible for monitoring, detecting, and responding to security incidents and threats. .SOC 2 is a standard for information security based on the Trust Services Criteria. It’s open to any service provider and is the one most commonly requested by potential customers. . To meet the Logical and Physical Access Controls criteria, one company might establish new employee onboarding processes, implement multi-factor authentication . Choose SOC 2 security controls that align with your organizational structure, ensuring they are relevant and effective in addressing your unique security and compliance requirements. . If you are using cloud providers like Amazon, you can request AOC and SOC reports to demonstrate their physical safety and server security controls.Common Criteria. AICPA Trust Services Criteria define five criteria for evaluating an organization’s security controls for SOC 2 compliance: security, availability, processing integrity, confidentiality, and privacy. While organizations may pick and choose which SOC 2 Trust Services Criteria they want to include in the scope of their audit .

Building out a security operations center is a major undertaking, but one that's well worth it when configured properly to provide adequate security for your enterprise. Building out a SOC requires careful planning and coordination of people, processes, and technologies. A fully-operational SOC will have the capabilities .
To address the question of “what are SOC 2 controls,” the four areas beyond the adapted COSO framework (and to which a label of SOC 2 controls list most apply) include logical and physical access, system and operations, change management, and risk mitigation controls. RSI Security’s SOC compliance services ensure optimal protection .A SOC is a centralized function or team responsible for improving an organization’s cybersecurity posture and preventing, detecting, and responding to threats. The SOC team, which may be onsite or outsourced, monitors identities, endpoints, servers, databases, network applications, websites, and other systems to uncover potential cyberattacks .
Simplify SOC 2 compliance with the right physical security systems. Genetec explains how service providers can stay SOC 2 compliant when it comes to data centre security. If the demand for cloud services was soaring before, then it has sky-rocketed in the past few years. According to Gartner, by 2025, 85% of infrastructure . When it comes to data security, the SOC 2 Trust Services Criteria (TSC) is one of the most critical standards. These standards cover everything from physical security to data encryption. There are five key categories in the TSC, listed below: Security. Security is defined as protecting databases and systems from unauthorized access .soc 2 physical security Physical Security: SOC 2 Control: Implement physical security measures to guard against unauthorized access to buildings, machinery, and sensitive data. ISO 27001 Control: Establish physical security perimeters, access controls, and monitoring systems to safeguard physical assets and avoid unauthorized access.Done-For-You (DFY) Professionally drawn Comprehensive and Robust SOC 2 Physical Security Guidelines is prepared by a committee of InfoSec Industry experts, Principal Auditors and Lead Instructors, under the .The SOC 2 is a report based on the Auditing Standards Board of the American Institute of Certified Public Accountants' () existing Trust Services Criteria (TSC).The purpose of this report is to evaluate an organization’s information systems relevant to security, availability, processing integrity, confidentiality, and privacy.soc 2 physical security What is SOC 2 The journey to SOC 2 compliance demands meticulous consideration of controls that encompass password security, security awareness training, employee access termination, physical access controls, incident response frameworks, multi-factor authentication, and much more.A security operations center (SOC) is a centralized unit responsible for monitoring and managing an organization's security posture. It is typically staffed by security professionals who are responsible for identifying, responding to and mitigating security threats. In short, a SOC team is responsible for making sure an organization is . The SOC 2 framework always includes a security audit, and the Security criterion defines several critical Common Criteria. Learn more here. Call +1 (888) 896-6207 for Continuum GRC Integrated Risk Management Solutions . The primary purpose of CC6 is to define the physical and logical security measures used to maintain authorized . The SOC 2 audit is a robust evaluation process, whether Type 1 (short-term) or Type 2 (long-term). So, to guarantee success, organizations should turn to a SOC 2 implementation guide —like this one. SOC 2 Implementation Guide for Service Organizations. SOC 2 is one of three primary System and Organization Controls (SOC) .It’s essential to follow these guidelines, implement security controls thoroughly, and consider your logical and physical access protocols from every angle. A thorough understanding of the protocols your organization needs to implement will help ensure you receive a clean SOC report. In short, the SOC 2 criteria expounds upon the idea that an .
Prime Numbers Facts: The only even prime number is 2 and the remaining even numbers can be divided by 2. So, it can’t be a prime number. No prime number greater than 5 ends with a 5. Since any number greater than 5 that ends with a 5 can be divided by 5, it can’t be a prime number. Zero and 1 are not prime numbers.
soc 2 physical security|What is SOC 2